Using nmap for Continuous vulnerability Monitoring
We will use nmap and Checkson for monitoring SSH daemons for CVEs.
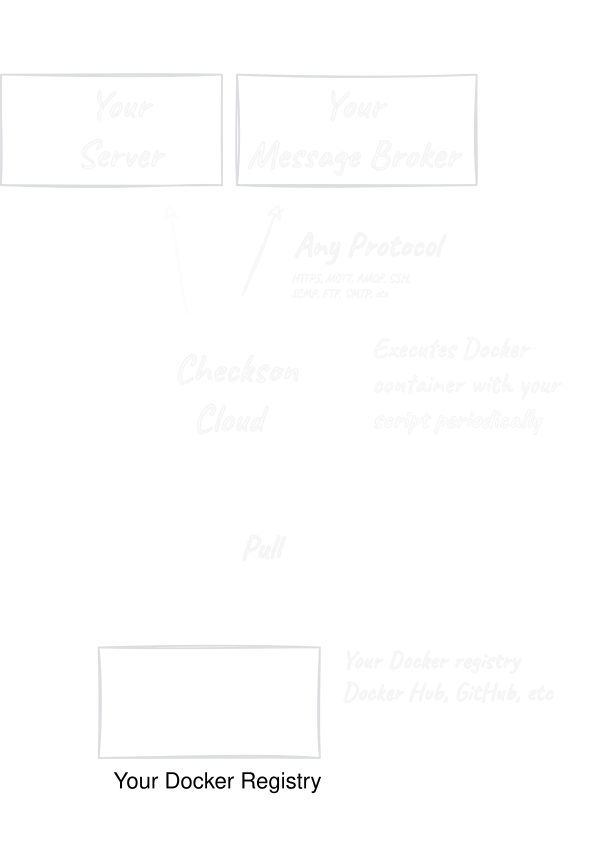
Checkson periodically runs your monitoring scripts written in e.g. Bash, Python, Javascript, Typescript wrapped in Docker containers and notifies you when they detect an issue using Slack, Email, PagerDuty and webhooks.
Features
A code-first approach to monitor the things you are responsible for
Thanks to Docker you can implement your check logic in any programming language you like. Most people use scripting languages such as Bash, Python, Javascript, Typescript or Ruby but you can also use compiled languages such as Go, Rust, C#, Kotlin or Java.
The Docker images of your checks do not have to be public. You can use private images from Docker registries such as Docker Hub, GitHub Container Registry, AWS ECR, Google Container Registry, Azure Container Registry, Quay.io, etc.
Checkson works well with GitHub and GitLab. You can build your Docker images using GitHub Actions or GitLab CI/CD and host them on the respective built-in registry. The meta-data of your check (e.g. how often it runs) can also be stored in your Git repository and applied using the Checkson CLI.
When your scripts detect that something is wrong, you are notified using PagerDuty, Slack, or E-Email. You can also forward notifications via webhooks, so you can integrate any tool you like.
There is a full-featured, single-binary command line client. This makes it possible to adopt a monitoring-as-code strategy.
There is a free plan that allows you to create two checks. They will be run with a maximum interval of 10 minutes. The free plan is not time-limited, you can use it as long as you want.
Step 1: Implement your check logic
Write your monitoring logic in a programming language of your choice. Most people use a scripting language such as Bash, Python, Javascript, Typescript or Ruby. Test locally until it works.
Step 2: Wrap it in a Docker container
Write a Dockerfile, build your image and push it to a Docker registry like Docker Hub.
Step 3: Create the check on Checkson
Configure your check using the CLI or the web-UI including notification channels.
Ready!
In this minimal example, a Python-based check is created that verifies if a website returns HTTP 200. You can see the Dockerfile for wrapping the code in a container and the shell commands used to setup the check on Checkson.
FROM python:3.10
COPY . /app
WORKDIR /app
RUN pip install requests
ENTRYPOINT ["python", "app.py"]
import os
import sys
import requests
URL = os.environ.get('TARGET_URL')
r = requests.get(URL)
if r.status_code == 200:
sys.exit(0)
else:
sys.exit(1)
> docker build . -t checkson/simple-check:1.0
> docker push checkson/simple-check:1.0
> checkson create simple-check \
--image checkson/simple-check:1.0 \
--env TARGET_URL=https://example.comHere are some things that you can use Checkson for
Use Lighthouse or Google's free PageSpeed Insights API to monitor the performance and technical SO properties of your website. See how it works.
Fill out your login form and check if access to the protected part of your website is granted. See how it works.
Use Playwright or Cypress to perform a complete checkout process including payment.
Check if your IoT device can connect to your MQTT broker and can send data. Check if that data can be queried via your REST API.
Use command line tools like testssl to check if your certificates are valid and that the settings of your webservers are safe.
Check if your ports are not exposing e.g. SSH to the Internet.
Test if important redirects, e.g. from your old URL to your new one, are working as they should. See how it works.
Use Node RED to implement your checks in a low-code manner.
Monitor if certain tags exist in your Docker Registry. See how it works.
We will use nmap and Checkson for monitoring SSH daemons for CVEs.
You have an IoT solution. It's important to your business, so you want it to be reliable. If you don't have end-to-end monitoring, it won't be.
FAQs
Checkson is well suited for implementing complex end-to-end checks. They can involve HTTPS, but also other protocols, such as SMTP, FTP, MQTT, AMQP, you name it.
Checkson is not meant to replace your infrastructure checks or your Kubernetes monitoring. There are better tools for this, e.g. Grafana/Prometheus.
The containers created from the image you configure are executed in our cloud environment. This means that you cannot access any internal services, but you should use the external interfaces of the system you are monitoring.
Yes, your container can only run for a limited amount of time (depending on the plan). By then it must have stopped with an exit-code indicating if the monitored system is healthy or not
Yes. You can run up to 2 checks for free. For more checks you can subscribe to a plan.
Yes, using the command line utility is optional. You can also configure checks using the web app.
You can create two checks for free. Both of these checks can run every 10 minutes (or less frequently).